In this article, we will demonstrate on how to find available M$ SQL servers within a network range and enumerate or get information about them.
Using Metasploit
msf > use auxiliary/scanner/mssql/mssql_ping
msf auxiliary(mssql_ping) > set RHOSTS <IP Address/range>
msf auxiliary(mssql_ping) > set THREADS 10
msf auxiliary(mssql_ping) > run
Using Nessus Cmd
#nessuscmd -i 10674 <IP range> --max-hosts 25
Using Nmap
#nmap -p 1434 --script ms-sql-info --script-args mssql.instance-port=1434 <IP range>
Using SQLRecon
Result of the Scan
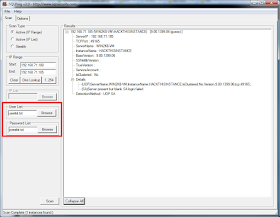
Using SQL Ping v3
SQL Ping v3 and SQL Recon has the same interface. The difference is that SQL Ping v3 has additional option for Brute Forcing Passwords with the ability to input the User and Password list.
Result of the Scan
Website: http://www.sqlsecurity.com/downloads
I will find more tools that can be used to gather information for SQL servers and will list them down here in future. If there's anything out there you readers are aware of, do share!






No comments:
Post a Comment