a bookworm who loves cyber security. a sucker for hacker and security conferences. loves attending and promoting conferences and has spoken at multiple conferences globally (almost). interests include cyber threat intelligence, cyber 'warfare', cyber 'terrorism' and cyber conflict.
Monday, 29 July 2013
Hackers - The Future Conquerors
The future conquerors will not be those who has the ability to buy modern technological weapons but those who could use a laptop to stop them.
Labels:
conquerors,
future,
geeks,
goths,
hackers,
huns,
modern,
technology,
vandals,
weapons
Sunday, 28 July 2013
Hacking Movie - Sneakers
Quotes from the movie Sneakers. Its amazing how real it means now..
"There's a war out there, old friend. A world war. And it's not about who's got the most bullets. It's about who controls the information. What we see and hear, how we work, what we think... it's all about the information!"
"The world isn't run by weapons anymore, or energy, or money. It's run by little ones and zeroes, little bits of data. It's all just electrons."
-- Cosmo from, "Sneakers" (1992)
Tuesday, 23 July 2013
Installing XAMPP and DVWA on BackTrack 5r3
What is DVWA? Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a class room environment.
A step by step guide on how to install XAMPP and DVWA on BackTrack Linux.
Before we begin, download the following:
> Xampp for Linux: http://www.apachefriends.org/en/xampp-linux.html#374
Once downloaded, put it into a folder in this case i created a folder in the Desktop called Tools. Then cd into the folder.
1. Provide write/modify access to the file
#chmod a+x xampp-linux-1.8.2-0-installer.run
2. Run the installation
#./xampp-linux-1.8.2-0-installer.run
Click Next
And Finish once done
A default XAMPP website will launch. Close the browser.
Start the XAMPP services
#/opt/lampp/lampp start
Open up your browser and type in http://localhost/ . You will see the XAMPP page
We are done for XAMPP. Now let's proceed to do the DVWA
Unzip the file
#unzip DVWA-1.0.7.zip
Move the folder to /opt/lampp/htdocs
On your browser, type in http://localhost/dvwa
Click on 'here' to create the database
Database created
Go back to the http://localhost/dvwa and enter the default credentials
username: admin
password: password
And we have installed DVWA and XAMPP on LINUX
NOW YOU HAVE MY PERMISSION TO HACK!!!!!!!!!!!
Sunday, 21 July 2013
Modem Authentication Bypass via Cookie ID 'Hijack'
In this 'hack', i am going to show how to bypass the authentication page of a modem by 'stealing' an authenticated session Cookie ID and apply it in our hack. For educational purpose and the potential of being sent a lawsuit and also as a form of respect to the company issuing these modems, i have removed all images of the company logo with the image 'CENSORED'.
The image of the Modem used in this 'hack'
Let's do the Modem Administration page walkthrough. Access the modem through the URL.
In this case, i want to edit some Wireless settings, so i click on the Wireless tab and it gives me a login portal. Enter my password and Login.
Once authenticated, i can now access the Wireless configuration settings.
Now let's do a wrong password authentication. Before doing this, we shall clear the browsing history including cookies from Firefox.
Browse to the login page and enter a wrong password. Since the password is invalid, we are now unable to login.
So let's try to bypass that login page. In this 'hack', im using Burp Proxy to analyze the HTTP header and perform the 'hijack'
Once Burp Proxy is configured, let's access the URL. Burp Proxy will show that we are making a request to the modem. Click Forward to let the traffic pass.
Next, a Cookie was created with the ID=dM4n1R
Go to the Wireless tab and enter the password.
When we click Login, it is using the same cookie to send the authentication details to the modem.
And since the password is correct, we are able to get the config_wifi.htm (which is the Wireless configuration page)
*Important: Copy the cookie ID!!!!! This is crucial for the bypass step.
And we are now in the configuration page.
Now let's clear our browsing history and cookies for a new session and this time we are going to analyse a failed authentication session.
Clear your cookies, close your browser and reopened it.
Access the URL and we now see a new cookie is being generated with the ID=a0SluW
Go to the Wireless tab and enter a wrong password.
Now since the password is wrong, we get the reply as config_wifi.htm?pwd=ko HTTP/1.1
And the message seen for a failed authentication.
Now let's perform the 'bypass hack'.
Clear the browsing histories and cookies. Close your browser and reopen a new one.
Access the URL.
You can see, a new session is created with a new cookie ID.
Replace the cookie ID with the ID dM4n1R
Replace the cookie ID with the ID dM4n1R when prompted
Now that all the cookies are replaced, click on the Wireless tab and you will see that you are able to access the Wireless Configuration page without having to authenticate at the login screen.
Conclusion
In this hack, while we practice the idea of deleting histories and cookies, some devices are not smart enough to know that the cookies used are a 'manipulated' one. Furthermore, in this administration page, there is no 'log out' button to be clicked. A possible prevention to this hack is to have the log out button which after that is smart enough to know that the cookie used after logged out must not be used anymore. Additionally, i would also need to mention that although this hack is successful, the same cookie ID could not be used after a period of time. The expiration of the cookie could be one of the reason why that happens.
*Disclaimer: While this hack is successful, my understanding on how cookies work in devices besides computers may not be correct hence my prevention suggestion may not be applicable to the modem device.
Labels:
authentication,
burp proxy,
bypass,
cookie,
hacking,
hijack,
modem,
password
Monday, 15 July 2013
Hacking Movie - Operation Takedown
Best Quote in the movie Operation Takedown that summarized the story of the infamous hacker and social engineer Kevin Mitnick
Hacker: You did not get this from me.I do not want Kevin Mitnick coming after me.
Tsutomu Shimomura: We respect your privacy
Hacker: Privacy? Never heard of it!
Friday, 12 July 2013
SPIDERING Website using Burp Spider
Burp Spider is a tool for automatically crawling web applications. While it is generally preferable to map applications manually, you can use Burp Spider to partially automate this process for very large applications, or when you are short of time. - http://portswigger.net/burp/help/spider_gettingstarted.html
Note: Using Burp Spider may result in unexpected effects in some applications. Until you are fully familiar with its functionality and settings, you should only use Burp Spider against non-production systems.
Before performing this, ensure that the proxy has been set and configured properly. Click here to know how to set the proxy up: http://securityg33k.blogspot.sg/2013/07/data-manipulation-intercepting-http.html
Click on Spider and Tick the 'spider running' option
In this example, we are not going to perform any traffic interception. Go to Proxy and ensure that the 'Intercept is Off'
In this example we are going to use a testing site by Acunetix: http://testphp.vulnweb.com
Now go to the 'Target' tab in Burp Suite and you will notice a set of links. Right click on the link that we want to spider and choose 'spider this host'
Now go to the 'spider' tab and you will notice the spidering action being performed.
Once done, go back to the 'Target' tab and expand the list under the site you Spidered. This will give us the list of items in the website for analysis and review.
Download Burp Suite here: http://www.portswigger.net/burp/download.html
Data Manipulation - Intercepting HTTP Traffic using Burp Suite Proxy
"Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities." - http://www.portswigger.net/burp/
Open Burpsuite in BackTrack
Click on the Proxy tab. By default, the settings is set to listening on port 8080.
Next, go to your browser and set your proxy settings to 127.0.0.1:8080
In this example, we are going to use a weakly configured test website to demonstrate what Burp Suite Proxy can do.
On your browser, go to www.bayden.com/sandbox/shop/ and click enter. You will notice that the website is trying to load..
Now, on Burp Suite, you will see that the traffic has been intercepted. You can see the data it is withholding. Click Forward to allow the traffic to go through.
On your browser, you will notice that the website now has loaded properly. Check out the price for the laptop... it costs $1095.
Let's try to change that shall we? Let's order 3 sets of it and click on Check Out.
On the Burp Suite Proxy, you will notice the HTTP traffic and what can we see here is the price of the laptop.
In the Params tab, you can see in a better format the cost of the laptop.
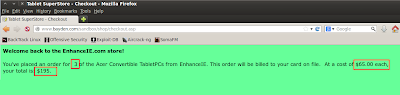
Let's change the price and put it to 65.00. Once changed, click forward.
And now you notice that you have successfully purchase 3 laptops for only $195.
------------------------------------------------------------------------------------------------------
Note: The site http://www.bayden.com/sandbox/shop/ is a site for testing, made available for those who wants to perform a POC (proof of concept) on this security issue.
Download Burp Suite here: http://www.portswigger.net/burp/download.html
Check out my previous blogpost on how to perform the same thing on Firefox and IE browser here: http://securityg33k.blogspot.sg/2013/07/5000-to-50-tamperingmanipulating-data.html
Labels:
backtrack,
burp suite,
data,
http,
intercepting,
linux,
manipulating,
proxy,
traffic
Subscribe to:
Posts (Atom)