Open Burpsuite in BackTrack
Click on the Proxy tab. By default, the settings is set to listening on port 8080.
Next, go to your browser and set your proxy settings to 127.0.0.1:8080
In this example, we are going to use a weakly configured test website to demonstrate what Burp Suite Proxy can do.
On your browser, go to www.bayden.com/sandbox/shop/ and click enter. You will notice that the website is trying to load..
Now, on Burp Suite, you will see that the traffic has been intercepted. You can see the data it is withholding. Click Forward to allow the traffic to go through.
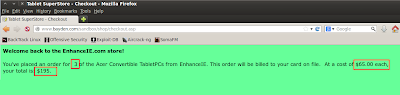
On your browser, you will notice that the website now has loaded properly. Check out the price for the laptop... it costs $1095.
Let's try to change that shall we? Let's order 3 sets of it and click on Check Out.
On the Burp Suite Proxy, you will notice the HTTP traffic and what can we see here is the price of the laptop.
In the Params tab, you can see in a better format the cost of the laptop.
Let's change the price and put it to 65.00. Once changed, click forward.
And now you notice that you have successfully purchase 3 laptops for only $195.
------------------------------------------------------------------------------------------------------
Note: The site http://www.bayden.com/sandbox/shop/ is a site for testing, made available for those who wants to perform a POC (proof of concept) on this security issue.
Download Burp Suite here: http://www.portswigger.net/burp/download.html
Check out my previous blogpost on how to perform the same thing on Firefox and IE browser here: http://securityg33k.blogspot.sg/2013/07/5000-to-50-tamperingmanipulating-data.html









No comments:
Post a Comment